Crippled systems, empty shelves, disappointed customers — all in the weeks leading up to Thanksgiving. It’s a nightmare scenario for every grocer, and a few months ago it became reality for Ahold Delhaize, which suffered a cyberattack that disrupted supply chain and e-commerce operations. The incident should serve as a flashing neon sign to industry peers that, almost certainly, they need to be devoting more attention to cybersecurity.
While it’d be comforting to think cybercriminals are only interested in defense contractors, banks, hospitals and casinos, it’s the harsh reality that many grocers are attractive targets.
Conditions that increase the likelihood of an incident include pharmacy services and the data that goes with them, third-party integrations that may not be properly secured, OT and IoT devices that may not be segmented from the corporate network, and many others.
Other weaknesses that create risk can stem from an incomplete “asset inventory,” which is problematic because, to do security well, you have to know what all you’re trying to secure.

How can grocers decrease the odds that cybersecurity incidents that have happened to others will happen to them? How can they improve their ability to respond swiftly and effectively if an attack occurs? CEOs can start by asking these five questions of their tech, security, and risk leaders.
1. What are our most significant vulnerabilities?
Every organization has vulnerabilities. They might include a weak configuration of tools and technologies; outdated systems, software or applications; or incomplete security coverage across assets. Other liabilities could be breakdowns in the processes of 1) vulnerability management — identifying soft spots for every asset — and 2) risk management — deciding whether and how to remediate each issue.
The companies best positioned to prevent attacks are the ones that know what their vulnerabilities are and implement a strong mechanism to prioritize and remediate them.
2. What programs and accountability measures do we have in place for cybersecurity training?
Many breaches happen because attackers trick an employee into providing access. Cybersecurity training is a simple but powerful defense — particularly when users are held accountable for timely completion of training. Another best practice is enhanced training for employees in the departments most likely to be targeted, such as finance and C-suite. Increased wariness among these employees is especially important given the continued increase in AI-powered attacks, such as deepfakes.
3. What proactive steps are we taking to ensure a quick recovery if an incident occurs?
Along with their efforts to prevent attacks, companies must also equip themselves to recover rapidly in the event of a breach to minimize harm to their operations and their customers. In November, a ransomware attack on a supply chain software provider forced U.K. grocer Morrisons to build a new warehouse management system after losing control of a network that spanned 21 warehouses handling its fresh food, produce, and bread. (You can read here about the remarkable recovery effort Morrisons and the provider made to resume normal operations.) In their case, swift action by a knowledgeable team allowed for business continuity alongside intense recovery efforts.
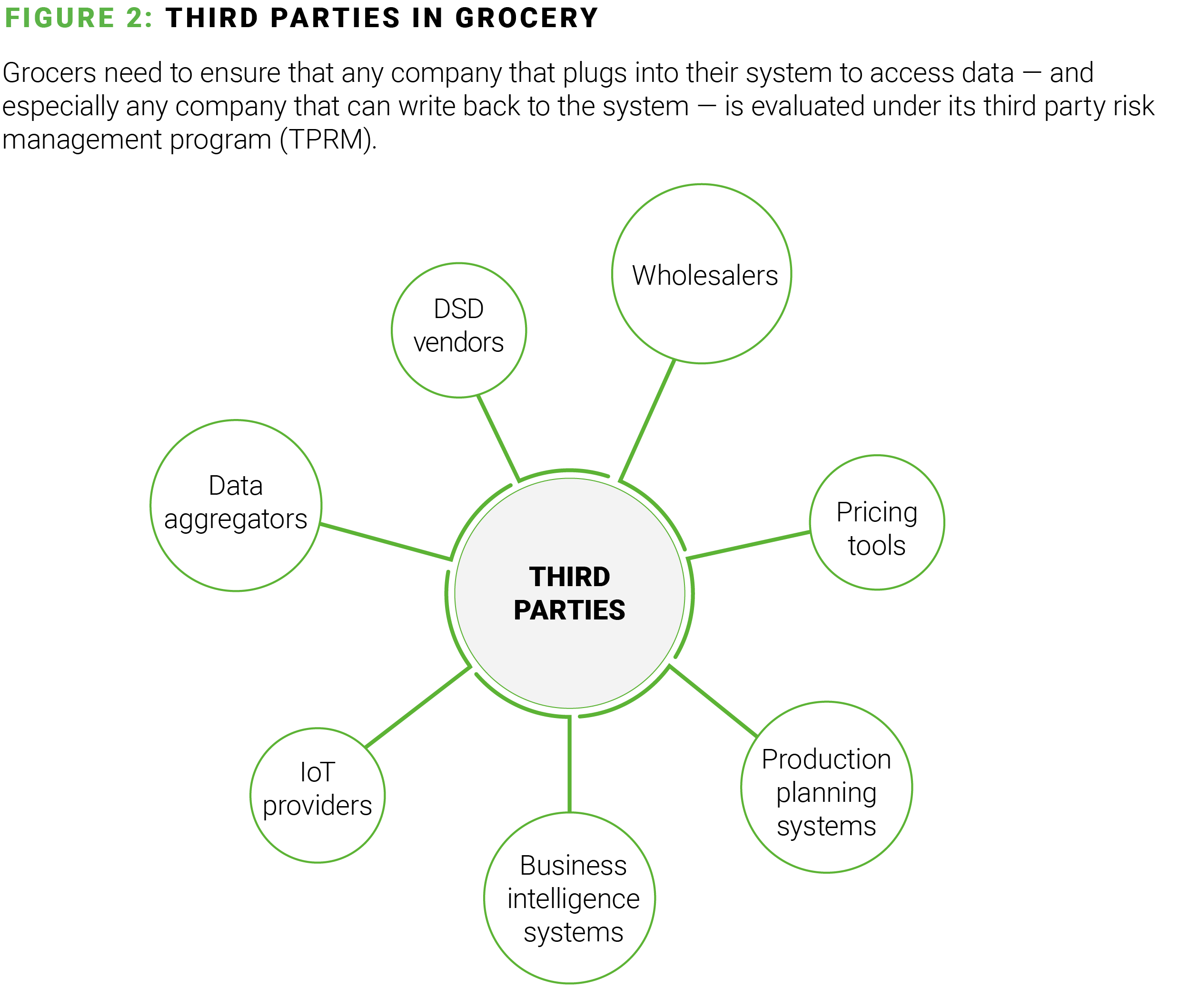
4. What is the current state of our third-party risk management (TPRM) program?
The sheer volume of third parties with which food and drug retailers interact can make assessing the risks associated with each partner feel overwhelming, but third parties that aren’t properly secured are ideal entry points for attackers, so it’s not an optional undertaking. Retailers must eliminate any TPRM assessment backlog that exists; streamline the process across risk functions (e.g., cybersecurity, privacy, anti-corruption, finance, etc.); and optimize the use of tools and technologies in the process.
5. What is our Operating Technology/Internet of Things (OT/IoT) security strategy?
Operating Technology and Internet-of-Things technology devices often present major security weaknesses, and attackers often use them to gain a foothold and pivot into the corporate network. Particularly because these devices play key roles in warehouse processes — the cessation of which would cause major disruption — companies should carefully evaluate how best to secure them.

A risk grocers must not take
As news reports and social media posts during previous incidents have made painfully clear, cyberattacks don’t only cause inconvenience and chaos for the company. They cause inconvenience and chaos for the customer. In today’s ultra-competitive food retail environment, that is a risk that grocers must not take.
There is a silver lining: The value of investments in cybersecurity can stretch far beyond attack prevention and emergency preparedness. When properly funded and part of a holistic strategy, cybersecurity can be a business enabler rather than just a compliance item. Stay tuned for our next article to learn how.





